Not known Factual Statements About Webintegrity
Table of ContentsGet This Report about WebintegritySome Known Incorrect Statements About Webintegrity The Ultimate Guide To Webintegrity
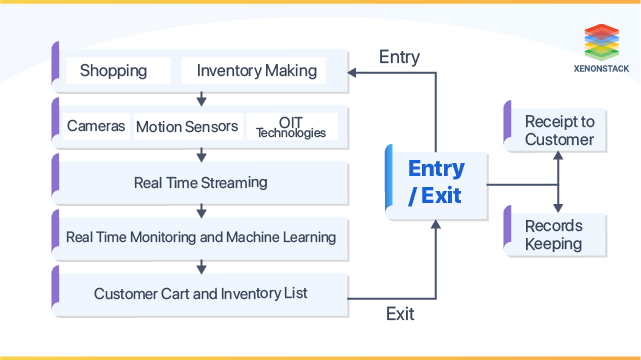
If you run a shopping business, you'll desire
to optimize your enhance to web servers issues prevent concerns, bandwidth overload and long loading lengthyPacking Monitoring your network in real time can expose workable insights about problems as well as efficiency ineffectiveness that need to be dealt with."Not only do organization leaders obtain to recognize the standing of their network efficiency and also safety and security at all times, yet when an incident takes place, the real-time notifying allows for faster case action, "stated Pieter Van, Iperen, creator and managing companion of PWV Consultants.
The 45-Second Trick For Webintegrity

It is necessary for organizations to resolve events as quickly as they occur, nevertheless huge or little they seem." When performance modifications or there is a protection alert, the system can alert you to ensure that repairs can be executed. This is why it is key to know what is normal for the business without recognizing what is regular, magnate have no concept just how to set signals (https://badbuyerlist.org/buyer/860630b7b74ccab19f823ff5)."There are a number of keeping track of applications on the marketplace, which vary in attributes, technical competence
and cost."I recommend selecting a solution that is easy to carry out and utilize. If you require much more intricate tools later, you can upgrade. There is a device to fit every circumstance.". By checking functional activities such as stock degrees or item use patterns, it becomes less complicated for managers at any type of degree to recognize which processes requirement renovation or optimization.
You can save time and resources by carrying out brand-new ones without first checking if those renovations will in fact lead to cost savings over time. Due to the nature of the BAM, managers
can react to these exceptions proactively as they can make use of real-time info. As an example, Cflow's BAM can be made use of to observe all your process-relevant tasks that happen across your organization. You can integrate task details and commute metrics and also execute business rules to set limits for simple visualization of the monitored information.
Company Refine Dimension(BPM )is a way to monitor click over here now and measure service procedures, which can be used for: Determining the efficiency of a procedure or procedure renovation. Automating organization procedures. A thing instance is a service things that has actually been instantiated in your system. It represents the tiniest device of organization process tracking, which can be used to monitor individual circumstances of a product by using its special identifier (ID). Utilizing just one KPI may not accurately mirror real state of either procedure. Utilizing numerous KPI metrics helps guarantee that administration has accessibility to pertinent details at all times throughout their everyday procedures. An essential efficiency sign( KPI )is a measurement of progression towards the accomplishment of a details objective. The most common sorts of KPIs consist of: Earnings targets Roi( ROI) metrics Revenue margin percentages Metricsare a means to measure and monitor the performance of an organization. Metrics are details to business and also should be defined prior to beginning any kind of BAM job. It is necessary that metrics be defined by the company customers, not IT or advertising professionals. g., when an email was sent out efficiently yet there was no recipient address saved for that person,this would certainly trigger the trigger to fire off a sharp concerning "no recipients". A debug log is generated after each occasion has happened. This helps you understand what occurred throughout that time duration without requiring any kind of additional details from individuals who logged into their accounts during those minutes. Without the debug log, it will become difficult to recover the lost information and to keep an eye on the changes that happened in between the events.